Create your first automation in just a few minutes.Try Studio Web →
PGP Encryption
by Internal Labs
1
Activity
2.9k
Summary
Summary
PGP Encryption custom activity built on the PGPCore library.
Overview
Overview
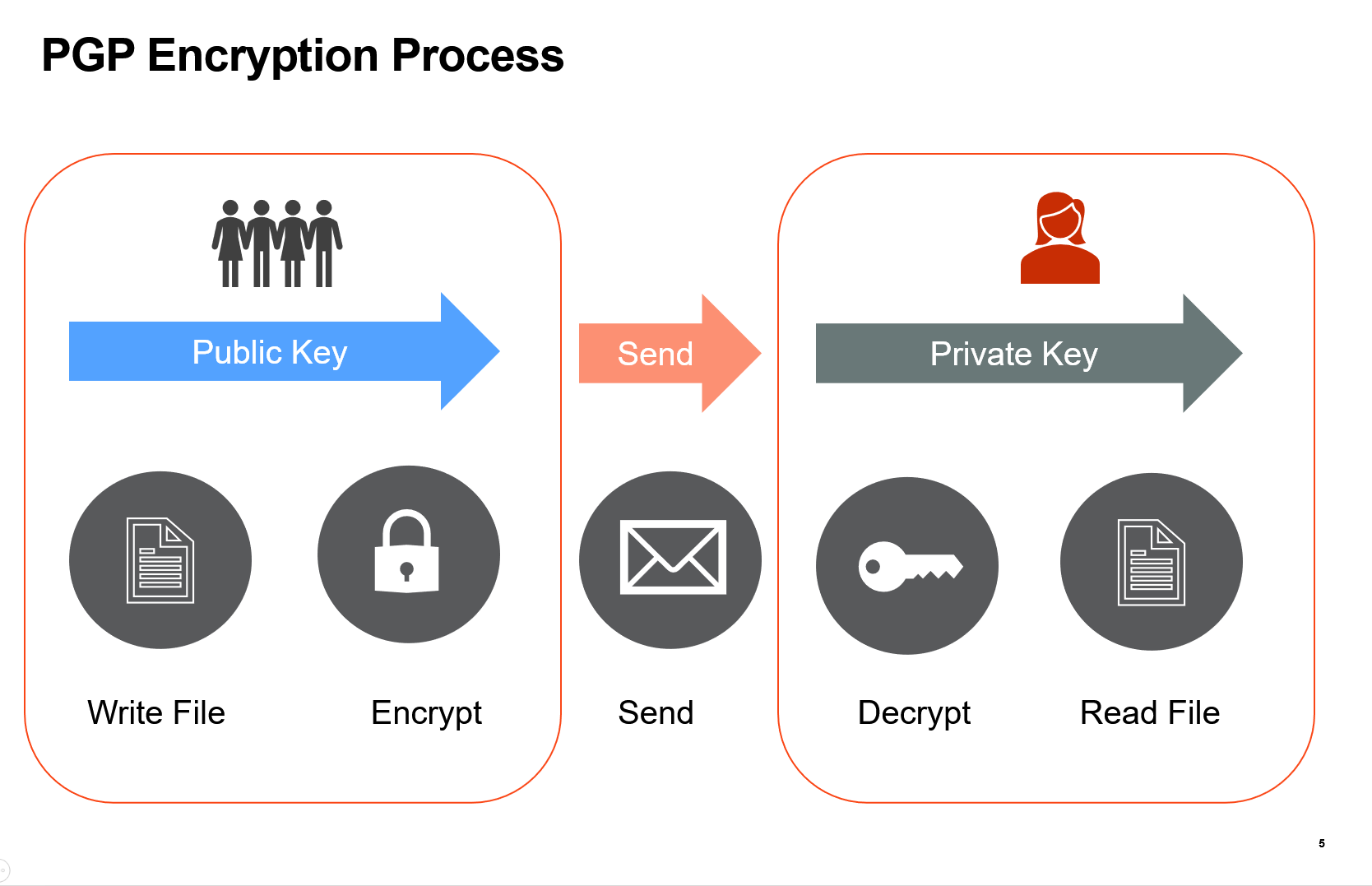
Use this activity to securely send, share, and store sensitive data on demand or in batch, verify data integrity and users as part of an automated robotic process, and generate PGP Keys pairs within your workflow - locally on your own machine. You can also cryptographically sign a document so that recipients can be verified - and have tampering detected.
- Generate a Key Pair: Generates a new public and private key for the provided username and password. Key size can also be specified.
- Encrypt File: Encrypts a file using a PGP Public Key. The path to save the encrypted file is required.
- Decrypt File: Decrypts an Encrypted File using your Private Key and Passphrase.
- Sign File: Cryptographically sign a file. The sender can be verified and tampering detected.
- Sign Clear File: Cryptographically sign a file. Leave the Text as human readable. The sender can be verified and tampering detected.
- Verify Sign: Verifies if a file or stream was signed by the matching private key of the counterparty.
- Verify Clear Sign: Verifies that a clear signed file or stream was signed by the matching private key of the counterparty.
- Encrypt and Sign: Encrypts a file using a public key and signs using your private key. The process is often that you encrypt with the public key of your counterparty and sign with your private key. Your counterpart would then decrypt with their private key and verify your signature with your public key.
- Decrypt and Verify: Decrypts and verifies the signature of an encrypted and signed file. This is used when your sender encrypts a document with your public key and then signs the encrypted document. You'd then decrypt the message with your private key and verify their identity with their public key.
- Verify Public Key: Verifies the validity of a public key.
Note: The PGP activities are offered to allow robots to interact directly with existing business processes that leverage PGP for privacy. They are not designed to provide new information security paradigms, but instead a means to allow the robot to interact with the existing security that is being deployed within a business.
Features
Features
- Intuitive and easy to use.
- Securely send, share, and store sensitive data.
- Perform Batch Encryption and Decryption.
- Generate PGP Key Pairs without using a 3rd Party service.
- Authenticate recipients.
- Sign messages and verify senders.
Additional Information
Additional Information
Dependencies
PgpCore >= 6.3.1
Code Language
C#, Visual Basic
Runtime
Windows (.Net 5.0 or higher)
Technical
Version
1.0.7Updated
February 5, 2024Works with
Studio: 23.10+
Certification
Silver Certified
Collections
Support
UiPath Community Support
Resources