Create your first automation in just a few minutes.Try Studio Web →
Security Orchestration Automation and Response
by UiPath
0
Solution
<100
Summary
Summary
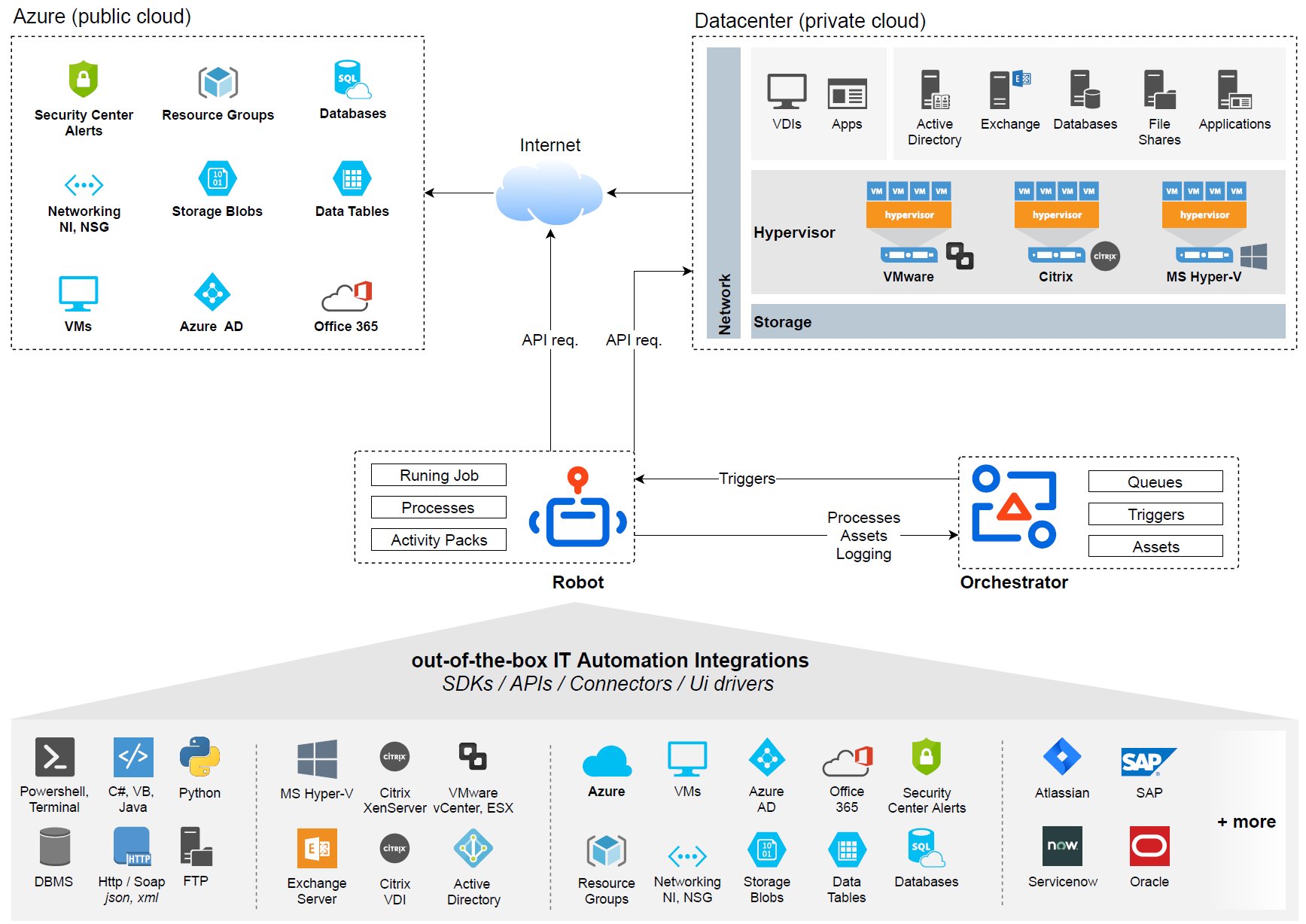
Workflow Solution built on top of the official UiPath IT Automation activities for automating the resolution of Azure brute force attacks security incidents targeting public facing virtual machines.
Overview
Overview
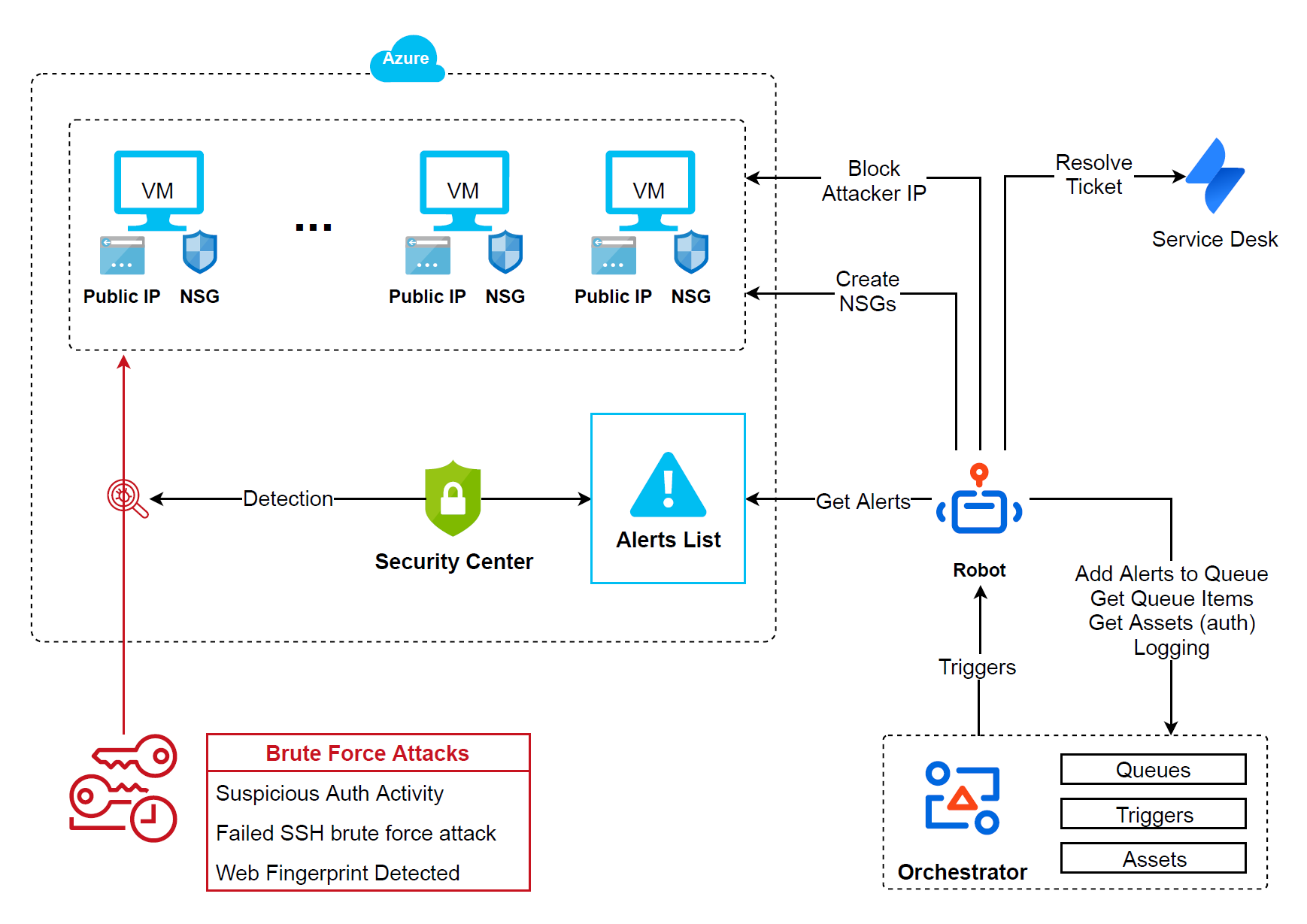
Azure public-facing Virtual Machines can be secured from brute force attacks with the solution’s ready to use workflows that block attacker IP addresses in the Virtual Machine’s Network Security Groups. The Azure Security Center Alerts types that can be processed automatically are:
- Suspicious authentication activity
- Possible incoming SQL brute force attempts detected
- Web Fingerprint Detected
- Failed SSH brute force attack
Solution Workflows:
1. AzureCreateNSGsForNIs
- creates NSGs for the Virtual Machines that don't have at least one associated with one of its Network Interfaces.
- (optional) it can be scheduled to run 1st - the other workflows will have no effect from a security resolution point of view if deny security rules cant be created for the attacked VM.
2. GetAzureSecurityCenterAlerts
- gets the Azure Security Center alerts for the supported Brute Force attack types and adds them to an Orchestrator Queue for processing.
3. AzureVMsAttackersBlock_AddSecurityRuleToNSG
- retrieves the pending Orchestrator queue items.
- the new Security Rules have their priority computed dynamically.
- if the attacker IP is already blocked in an NSG, it will be skipped.
4. Block_AttackerIP_in_VM_NSGs
- the workflow can be executed on-demand from the Orchestrator web or mobile apps.
- the specified IP is blocked in all the Network Security Groups associated with the input Virtual Machine.
Features
Features
The solution works like a digital cyber-security officer that resolves the supported brute force attacks 24/7, thereby increasing your organization's cloud security. Also, the workflows are easy to integrate with existing ITSM ecosystems for end to end security incident management.
Additional Information
Additional Information
Dependencies
UiPath.Azure.Activities (>=1.1.0)
Code Language
Visual Basic
License & Privacy
MIT
Privacy Terms
Technical
Version
1.1Updated
June 14, 2023Works with
Studio: 21.10 - 22.10
Certification
Silver Certified
Collections
Support
UiPath Community Support
Resources